Hey all,
As most of you know, a Trojan was recently discovered in the software for Energizer’s USB battery charger. Following its release, I wrote an Nmap probe to detect the Trojan and HDMoore wrote a Metasploit module to exploit it.
I mentioned in my last post that it was a nice sample to study and learn from. The author made absolutely no attempt to conceal its purpose, once installed, besides a weak XOR encoding for communication. Some conspiracy theorists even think this may have been legitimate management software gone wrong – and who knows, really? In any case, I offered to write a tutorial on how I wrote the Nmap probe, and had a lot of positive feedback, so here it is!
Just be sure to take this for what it is. This is not intended to show any new methods or techniques or anything like that. It’s a reverse engineering guide targeted, as much as I could, for people who’ve never opened IDA or Windbg in their lives. I’d love to hear your comments!
Sections
This tutorial was getting far too long for a single page, so I broke it into four sections:
- Part 1: setup
- Part 2: runtime analysis (windbg)
- Part 3: disassembling (ida)
- Part 4: generating probes (nmap)
Step 0: You will need...
To follow along, you’ll need the following (all free, except for Windows itself):
- A disposable Windows computer to infect (probably on VMWare)
- Debugging Tools for Windows (I used 6.11.1.404)
- IDA (free)
- Nmap
- A basic understanding of C and x86 assembly would be an asset. <shamelessplug>Check out the reverse engineering guide I wrote</shamelessplug>
- A basic understanding of the Linux commandline (gcc, pipes, etc)
Infect a test machine
The goal of this step is, obviously, to infect a test system with the Energizer Trojan.
Strictly speaking, this isn’t necessary. You can do a fine job understanding this sample without actually infecting yourself. That being said, this Trojan appears to be fairly safe, as far as malware goes, so it’s a good one to play with. I strongly recommend against installing this on anything other than a throwaway computer (I used VMWare). Do not install this on anything real. Ever. Seriously!
If you’re good and sure this is what you really want to do, grab the file here:
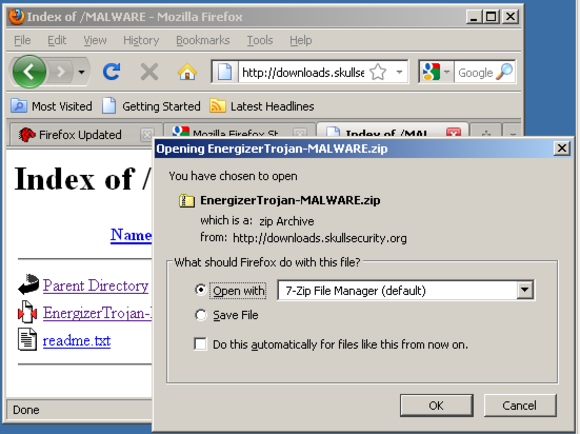
Then extract the installation file, UsbCharger_setup_v1_1_1.exe (arucer.dll isn’t necessary yet). The password for the zip archive is “infected”, and by typing it in you promise to understand the risks of dealing with malware:
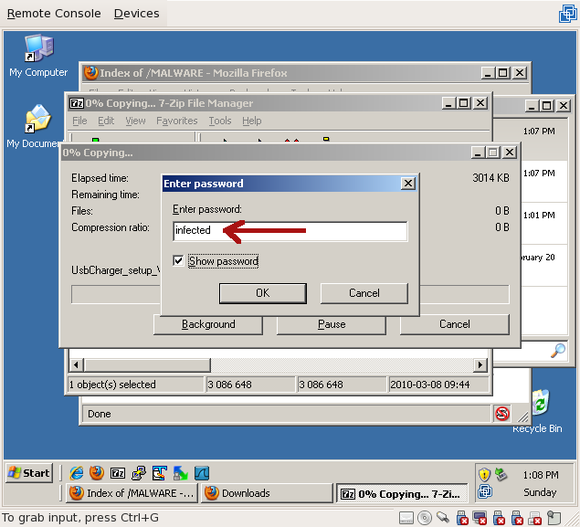
Naturally, make sure you turn off antivirus software before extracting it. In fact you shouldn’t even be running antivirus because your system shouldn’t even be connected to the network!
Perform a typical install (ie, hit ‘next’ till it stops asking you questions). Once you’ve finished the installation, verify that the backdoor is listening on port 7777 by running “cmd.exe” and running “netstat -an”:
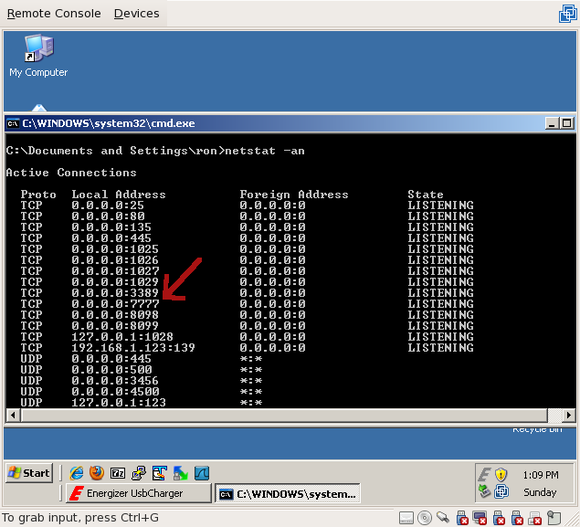
Congratulations! Your system is now backdoored. To continue reading, go to Part 2: runtime analysis

Comments
Join the conversation on this Mastodon post (replies will appear below)!
Loading comments...